-
How to Search Reviews on Google Maps
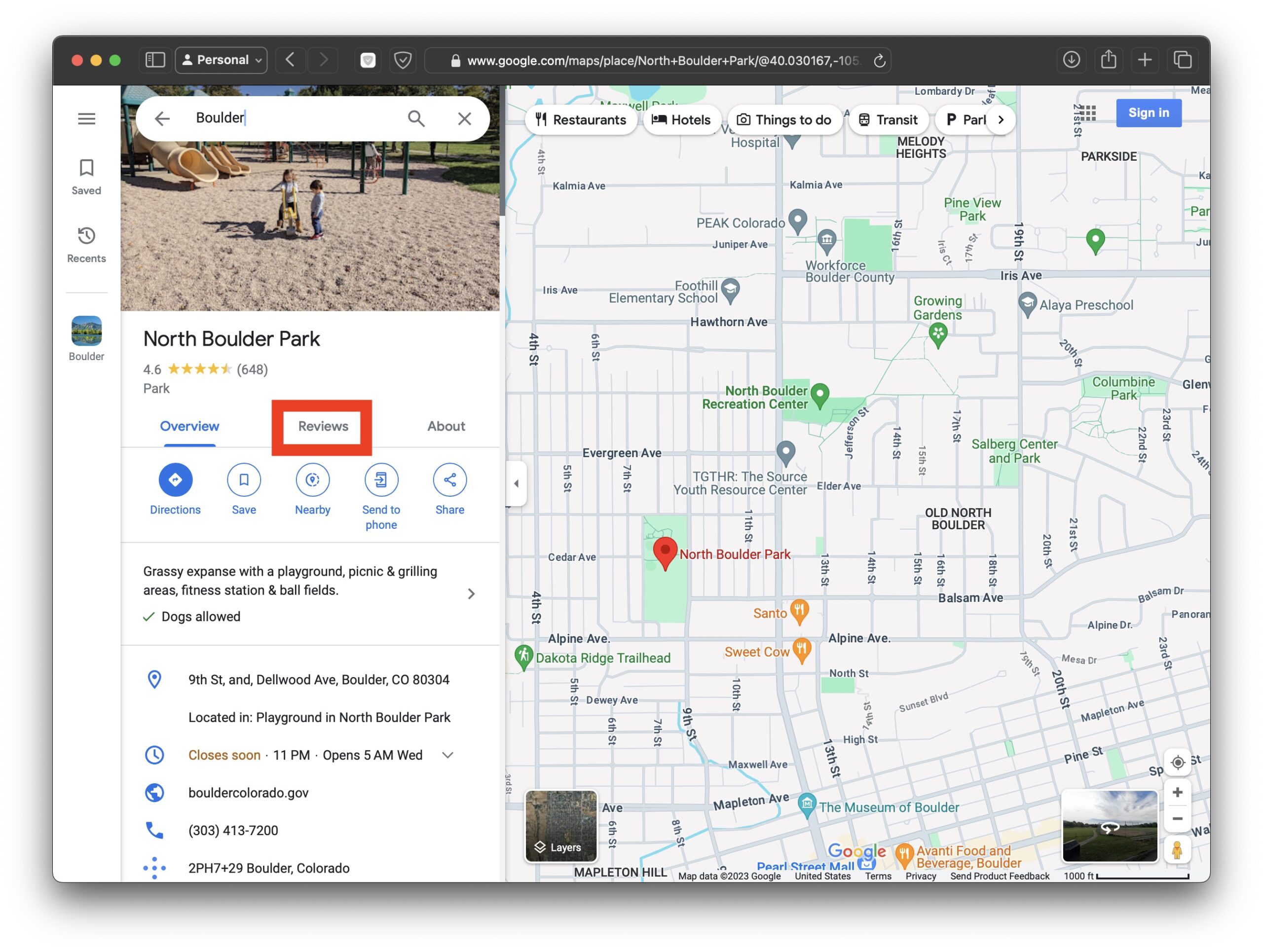
Go to OSX Daily to read How to Search Reviews on Google Maps Many people use Google Maps to find out about businesses, parks, locations, and destinations, by reading the reviews. While it’s one thing to browse through all of the reviews and read them, it can be very useful to narrow down reviews for…
-
How to Sync Google Contacts to iPhone or iPad

Go to OSX Daily to read How to Sync Google Contacts to iPhone or iPad Do you have a bunch of contacts in Gmail or with a Google account that you want to sync to your iPhone or iPad? While you may have already added a Gmail account to your iPhone or iPad when setting…
-
How to Use Translation Apps and Extensions Without Sacrificing Your Privacy

Read full article: at LifeHacker When you want to translate something, the easiest option is often a free translation service like Google Translate. But you should avoid pasting sensitive information into free translation services, as your data could end up in the public domain or used for advertising. (Generally, if you have highly sensitive… Read…
-
How to Update Your AirPods

Read full article: at LifeHacker Apple often issues firmware updates for its entire AirPods line, including AirPods Pro, AirPods 2, AirPods 3, and AirPods Max. However, the company doesn’t make it clear how to actually update your AirPods, nor do they share what each firmware update does. So here’s how to do it, whatever model…
-
How to Hum to Search Songs with Google

Go to OSX Daily to read How to Hum to Search Songs with Google Ever had a song stuck in your head you don’t know the words to? Don’t know the lyrics of a song quite enough to find it on the web by just typing the lyrics? Google has a solution for you. The…