-
3 Ways to Unblock YouTube & Watch Blocked Videos from Any Device

Go to OSX Daily to read 3 Ways to Unblock YouTube & Watch Blocked Videos from Any Device Many networks will block YouTube for any number of reasons; maybe you’re in a region or country where YouTube is not allowed, maybe you’re at a school or institution where YouTube is blocked, maybe censorship is blocking…
-
How to Autofill Security Codes from Mail on Mac, iPhone, iPad
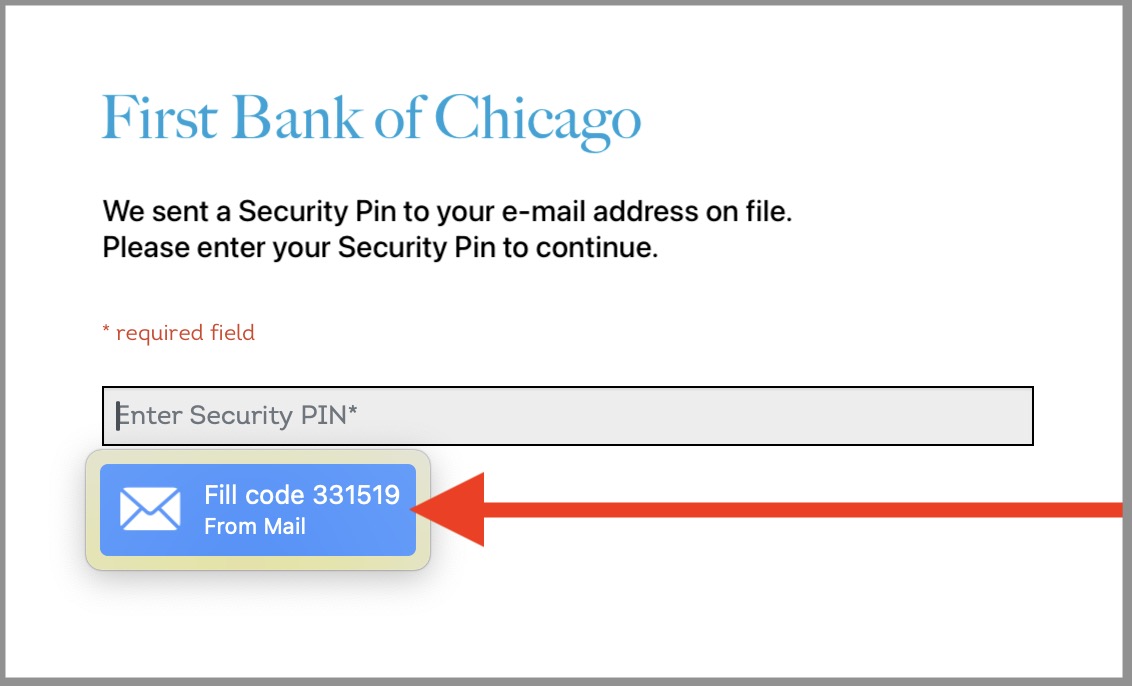
Go to OSX Daily to read How to Autofill Security Codes from Mail on Mac, iPhone, iPad The latest versions of Mail for iPhone, Mac, and iPad support a fantastic autofill security code feature. This is similar to the autofilling security code feature for SMS that is available in Messages for Mac, iPhone, and iPad,…
-
Safari Autofill Security Codes Not Working on Mac? Here’s a Tip
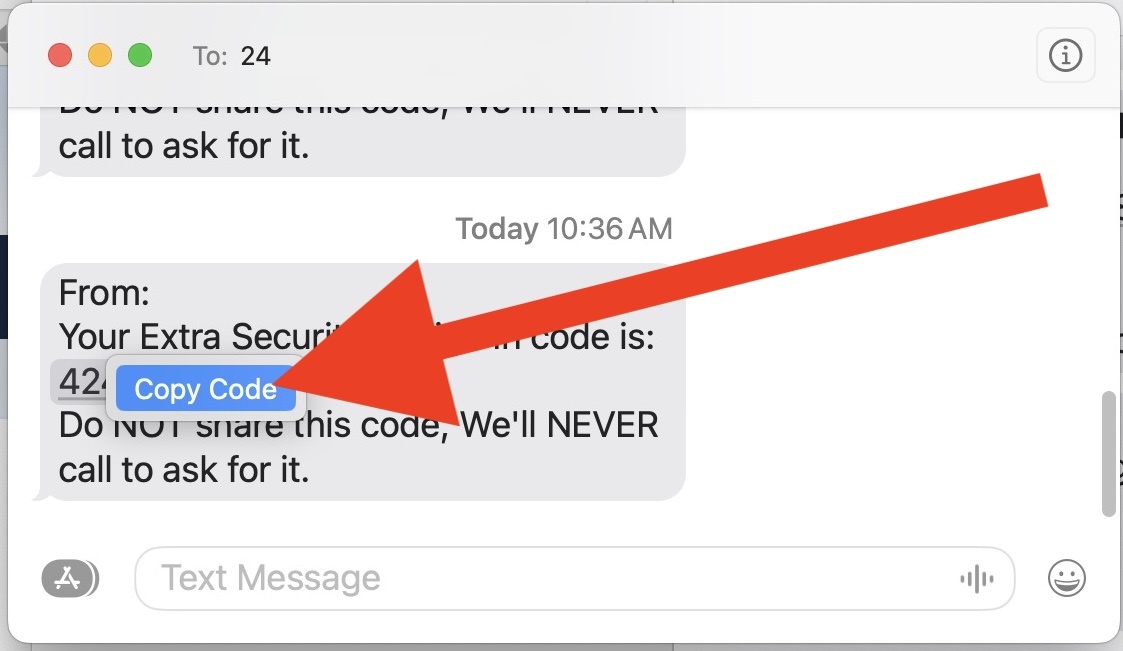
Go to OSX Daily to read Safari Autofill Security Codes Not Working on Mac? Here’s a Tip Modern versions of Safari for Mac include an incredibly useful Autofill Security Code feature, that allows security codes that are texted to your number to be automatically filled in when you are logging into secure websites in Safari…
-
How to Stop iPhone Apps Snooping via Push Notifications
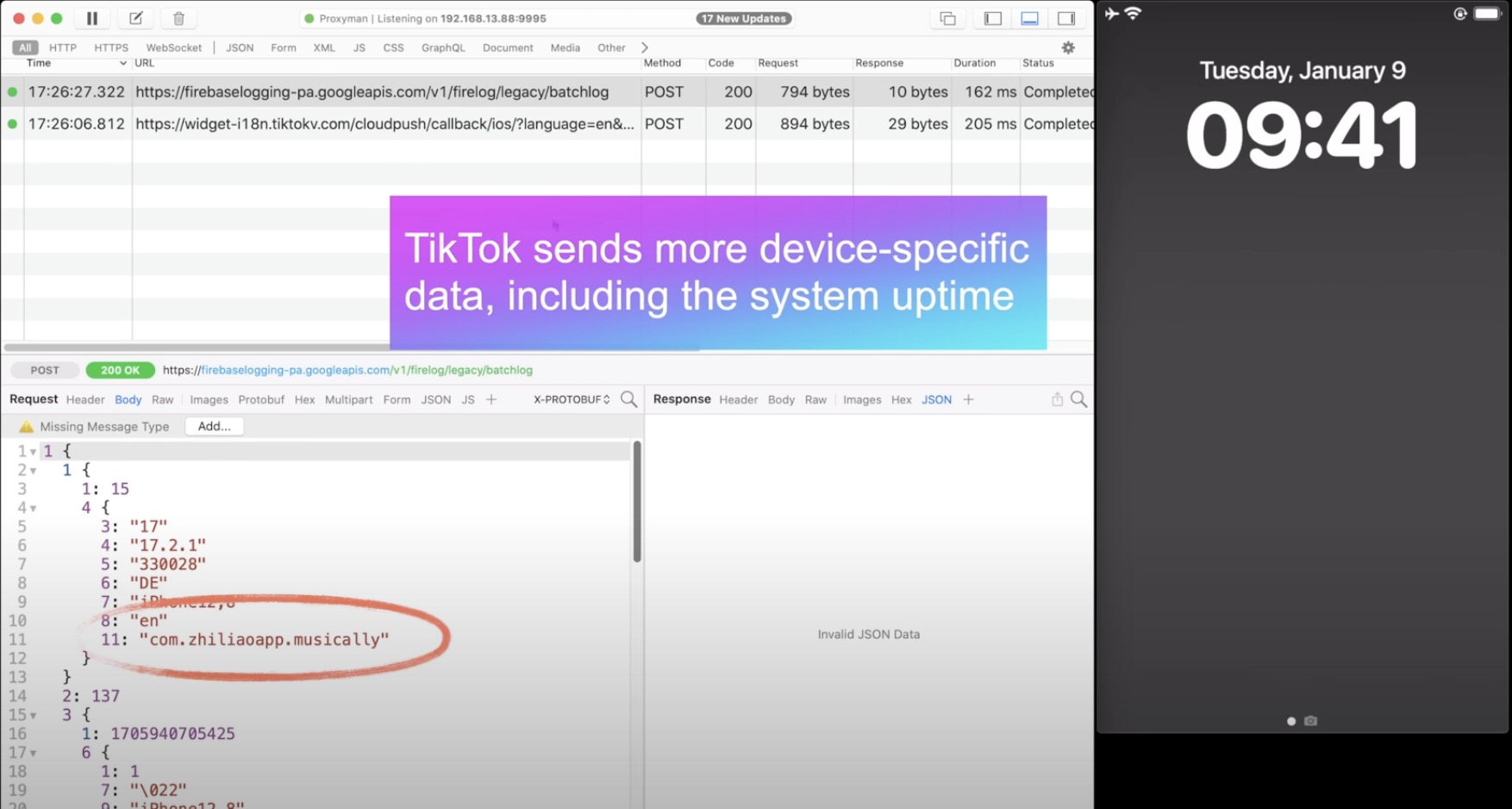
Go to OSX Daily to read How to Stop iPhone Apps Snooping via Push Notifications Apple is well known for being a privacy centric company and building tons of security and privacy features into the iPhone and iPad to control things like location tracking and app tracking, but some big name app developers are coming…
-
How to Stop iPhone Siri Listening to You

Go to OSX Daily to read How to Stop iPhone Siri Listening to You Due to the nature of how Hey Siri on iPhone works, Siri is basically always listening to you and your surroundings, if the Hey Siri feature is enabled. This is necessary to hear the “Hey Siri” activation word so that Siri…
-
Content Blockers May Break Captive Portal Wi-Fi Login Pages
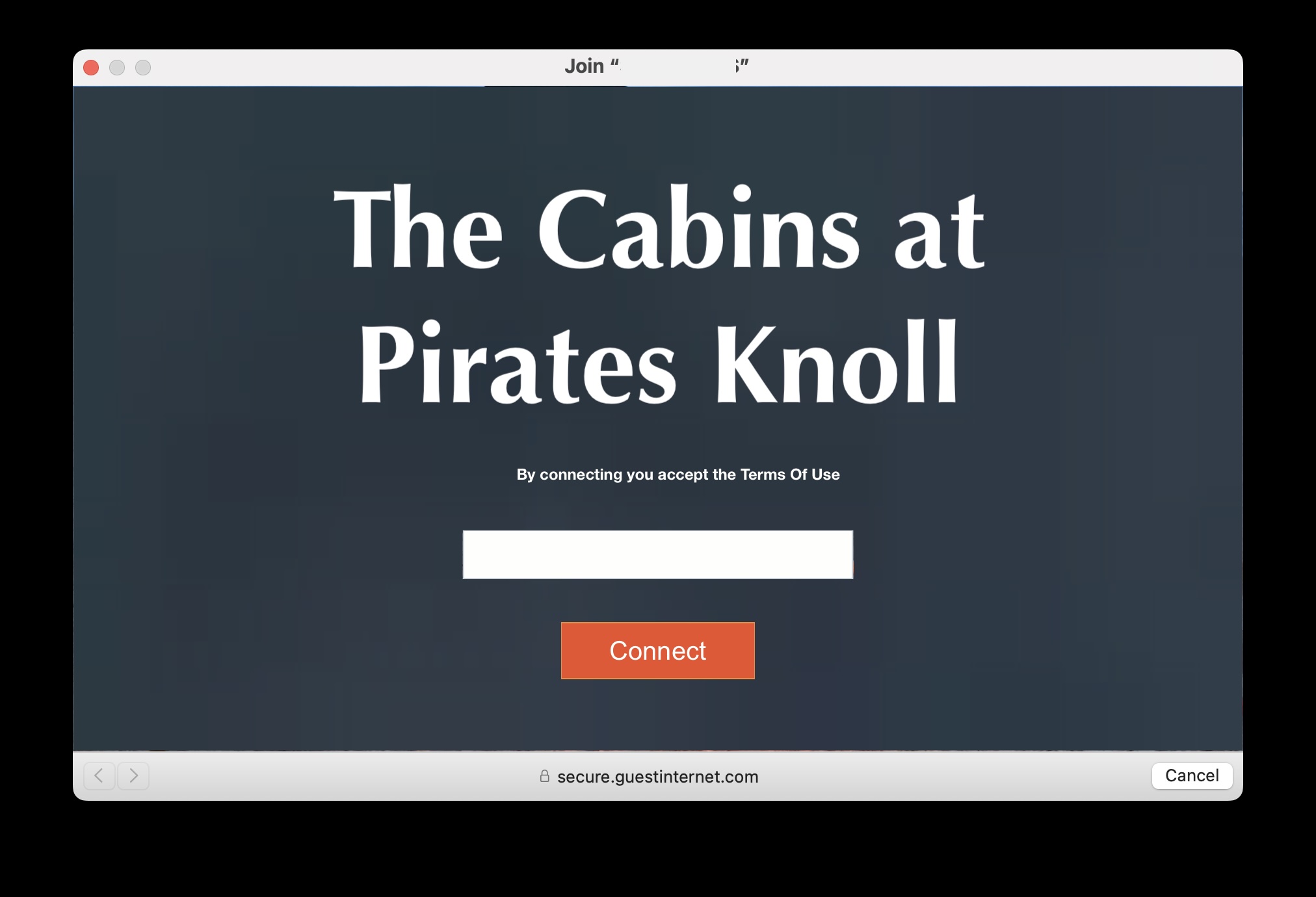
Go to OSX Daily to read Content Blockers May Break Captive Portal Wi-Fi Login Pages Here’s a helpful bit of knowledge that you may want to keep in mind when traveling or using public wi-fi spaces; if you use Content Blockers in Safari or your web browser, that content blocker may break a wi-fi’s captive…
-
5 iCloud Security Features You Should Be Using
Go to OSX Daily to read 5 iCloud Security Features You Should Be Using iCloud is packed full of features that make using devices in the Apple ecosystem super easy and fluid, but there are some security features and capabilities offered by iCloud that literally everyone should be using because of their added benefits to…
-
9 Tips for Staying Safe Online with Your iPhone, Mac, or iPad

Go to OSX Daily to read 9 Tips for Staying Safe Online with Your iPhone, Mac, or iPad Staying safe online with your Apple devices is an ongoing effort, and it’s important to keep yourself vigilant and informed about potential threats and risks. While the Mac, iPhone, and iPad, are generally much more secure than…


